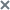Viewing a TAA (IOA) rule added to exclusions
Viewing a TAA (IOA) rule added to exclusions
8 November 2023
ID 247782
To view a TAA (IOA) rule added to exclusions:
- In the application web interface window, select the Settings section, Exclusions subsection and go to the TAA exclusions tab.
The table of excluded TAA (IOA) rules is displayed.
- Select the rule that you want to view.
This opens a window containing information about the rule.
The window contains the following information:
- TAA (IOA) rule: click this link to open a window containing a description of the MITRE technique corresponding to this rule, recommendations on responding to the event, and information about the likelihood of false alarms.
- ID is the ID that the application assigns to each rule.
- Name is the name of the rule that you specified when you added the rule.
- Importance is an estimate of the probable impact of the event on the security of computers or the corporate LAN as assessed by Kaspersky experts.
- Confidence is the level of confidence depending on the probability of false positives as estimated by Kaspersky experts.
- Exclude rule is the operating mode of the rule that is added to exclusions.
- Always means the rule is always excluded. In this case, Kaspersky Anti Targeted Attack Platform does not mark events as matching the TAA (IOA) rule and does not create alerts based on that rule.
- Based on conditions means the rule is excluded if a condition is added. In this case, the TAA (IOA) rule is supplemented by conditions in the form of a search query. Kaspersky Anti Targeted Attack Platform does not mark events that match specified conditions as matching the TAA (IOA) rules. For events that match the TAA (IOA) rule, but do not satisfy the conditions of the applied exclusion, the program marks the events and creates alerts.
- Configure additional conditions: click this link to open the event search form with search conditions.
The field is displayed if, when adding the TAA (IOA) rule to exclusions, you have selected the Based on conditions mode, and configured some search criteria.
- The search criteria are configured in the
<IOA ID> AND NOT <search criteria>format.Search criteria are displayed if, when adding the TAA (IOA) rule to exclusions, you have selected the Based on conditions mode, and configured some search criteria.
- Apply to servers* are hosts to which the exclusion applies.
This field is displayed in distributed solution and multitenancy mode.
Did you find this article helpful?
What can we do better?
Thank you for your feedback! You're helping us improve.
Thank you for your feedback! You're helping us improve.