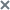Viewing the TAA (IOA) rule table
8 November 2023
ID 247701
If you are using the distributed solution and multitenancy mode, use the web interface of the PCN or SCN server for which you want to configure parameters.
The table of user-defined TAA (IOA) rules contains information about TAA (IOA) rules that are used to scan events and create alerts; the table is in the Custom rules section, TAA subsection of the application web interface window.
The table contains the following information:
 —Importance level that is assigned to an alert generated using this TAA (IOA) rule.
—Importance level that is assigned to an alert generated using this TAA (IOA) rule.The importance level can have one of the following values:
 – Low.
– Low. – Medium.
– Medium. – High.
– High.
- Type is the type of the rule depending on the operating mode of the application and the role of the server which generated the rule:
- Global—Created on the PCN server. These rules are used to scan events on this PCN server and all SCN servers connected to this PCN server. Scanned events belong to the tenant which the user is managing in the program web interface.
- Local—Created on the SCN server. These rules are used to scan events on this SCN server. Scanned events belong to the tenant which the user is managing in the program web interface.
- Confidence – level of confidence depending on the likelihood of false alarms caused by the rule:
- High.
- Medium.
- Low.
The higher the confidence, the lower the likelihood of false alarms.
- Name – name of the rule.
- Servers are names of servers with the PCN or SCN role to which the rule applies.
This column is displayed if you are using the distributed solution and multitenancy mode.
- Generate alerts – requirement to store information on alerts based on matching an event from the database with criteria of the rule.
- Enabled – a record is created for the event in the alerts table with Targeted Attack Analyzer (TAA) technology specified.
- Disabled – not displayed in the alert table.
- State – usage status of the rule in event scans:
- Enabled – the rule is being used.
- Disabled – the rule is not being used.