How to protect against the WannaCry attacks if you use Kaspersky solutions for business
Kaspersky engineers have analyzed the information on the cases of infection with the WannaCry file-encrypting malware, which attacked a number of companies around the world on May, 12.
The attack was implemented through the Microsoft Security Bulletin MS17-010 network vulnerability. The rootkit was installed on the infected computers, through which the file-encrypting malware was run.
All Kaspersky solutions now detect this rootkit as MEM:Trojan.Win64.EquationDrug.gen. Kaspersky solutions also detect the encryption malware which was used during this attack under the following names:
- Trojan-Ransom.Win32.Scatter.uf
- Trojan-Ransom.Win32.Scatter.tr
- Trojan-Ransom.Win32.Fury.fr
- Trojan-Ransom.Win32.Gen.djd
- Trojan-Ransom.Win32.Wanna.b
- Trojan-Ransom.Win32.Wanna.c
- Trojan-Ransom.Win32.Wanna.d
- Trojan-Ransom.Win32.Wanna.f
- Trojan-Ransom.Win32.Zapchast.i
- Trojan.Win64.EquationDrug.gen
- PDM:Trojan.Win32.Generic
- Intrusion.Win.DoublePulsar.a
We recommend that the companies perform the following actions to minimize the risk of infection:
- Install the official Microsoft patch, which fixes the vulnerability exploited by this malware:
- Make sure anti-malware solutions are enabled on all nodes in the network.
- Update databases of all Kaspersky solutions used.
To view the detailed guide for your Kaspersky solution, see the section How to avoid network infection later in this article.
Kaspersky experts are currently analyzing the malware samples to find decryption options.
For detailed information about the WannaCry attacks, please refer to the Kaspersky report.
How to disinfect the network if you use a Kaspersky anti-malware solution
Kaspersky Endpoint Security 8/10
- Disconnect the infected computer from the corporate network.
- Install the Microsoft patch:
- Make sure the System Watcher component and all its modules are enabled:
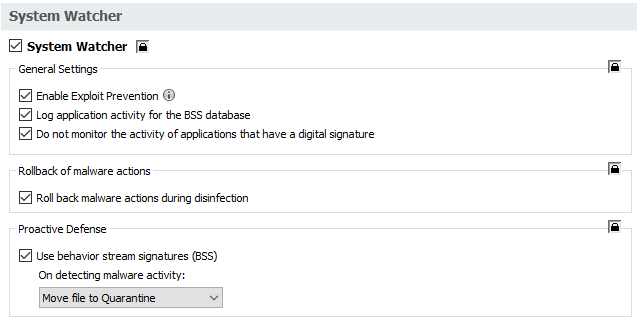
- Make sure Network Attack Protection is enabled.
- Make sure File Anti-Virus is enabled.
- Run the Critical Areas Scan task to detect the infection as early as possible.
- Upon detection of MEM:Trojan.Win64.EquationDrug.gen, restart the computer.
- Run a full scan to delete the malware.
- Connect the computer to the network.
Kaspersky Security 10 for Windows Server:
- Disconnect the infected computer from the corporate network.
- Install the Microsoft patch:
- Make sure the Real-time file protection component is enabled.
- Set the application according to the recommendations from this article. This will help you protect the server from being remotely encrypted from hosts which have access to it.
- Run the Critical Areas Scan task to detect the infection as early as possible.
- Upon detection of MEM:Trojan.Win64.EquationDrug.gen, restart the computer.
- Run a full scan to delete the malware.
- Connect the computer to the network.
Anti-Virus 8.0 for Windows Servers EE:
- Disconnect the infected computer from the corporate network.
- Install the Microsoft patch:
- ake sure the Real-time file protection component is enabled.
- Run the Critical Areas Scan task to detect the infection as early as possible.
- Upon detection of MEM:Trojan.Win64.EquationDrug.gen, restart the computer.
- Run a full scan to delete the malware.
- Connect the computer to the network.
How to disinfect the network if you use other anti-malware solutions
Locally:
- Disconnect the infected computer from the corporate network.
- Install the Microsoft patch:
- Run a scan in Kaspersky Virus Removal Tool.
- Upon detection of MEM:Trojan.Win64.EquationDrug.gen, restart the computer.
- Run a full scan to delete the malware.
- Connect the computer to the network.
Remotely:
- Install the Microsoft patch:
- Move the Kaspersky Virus Removal Tool executable file to a shared folder.
- Run the tool on a remote computer (through remote command line, a group policy or a .bat file in Kaspersky Security Center) using the command:
\\share\kvrt.exe -accepteula -silent -dontcryptsupportinfo -d \\share\logs\%COMPUTERNAME%
- share — shared folder name.
- When you execute this command on a remote computer, the scan will be performed without disingection and the process log will be created in \\share\logs\
- For disinfection, add the parameters -adinsilent -processlevel 1 to the command
\\share\kvrt.exe -accepteula -silent -adinsilent -processlevel 1 -dontcryptsupportinfo -d \\share\logs\%COMPUTERNAME%
- Upon detection of MEM:Trojan.Win64.EquationDrug.gen, restart the computer.
How to use Kaspersky Rescue Disk
- Disconnect the infected computer from the corporate network.
- Install the Microsoft patch:
- Boot the computer from the Kaspersky Rescue Disk installer.
Kaspersky Rescue Disk 10 is incompatible with RAID. For more information, please refer to the system requirements.
- Run a scan task. For the guide on how to run a scan task, please see this article.
- Upon detection of MEM:Trojan.Win64.EquationDrug.gen, restart the computer.
- Run a full scan to remove the malware.
- Connect the computer to the network.
How to prevent the infection
Kaspersky Endpoint Security 8/10:
- Install the Microsoft patch:
- Make sure System Watcher and its modules are enabled:

- Make sure Network Attack Protection is enabled.
- Make sure File Anti-Virus is enabled.
- Update anti-malware databases.
Kaspersky Security 10 for Windows Server:
- Install the Microsoft patch:
- Make sure the Real-time file protection component is enabled.
- Set the application according to the recommendations from this article. This will help you protect the server from being remotely encrypted from hosts which have access to it.
- Update anti-malware databases.
Anti-Virus 8.0 for Windows Servers EE:
- Disconnect the infected host from the network.
- Install the Microsoft patch:
- Make sure the Real-time file protection component is enabled.
- Update anti-malware databases.
Kaspersky Anti-Virus 6.0 R2 for Windows Workstations:
- Disconnect the infected host from the network.
- Install the Microsoft patch:
- Make sure File Anti-Virus is enabled.
- Make sure the Anti-Hacker component is enabled.
- Update anti-malware databases.
How to distribute the Microsoft update through Kaspersky Security Center
Main way:
- Download the updates from the Microsoft websites:
- Create a temporary folder on a local drive and move the downloaded *.msu files to it.
- In the temporary folder, create a .bat file. Open the file for editing and type a command of the following format:
wusa.exe "%cd%\updatename.msu" /quiet /warnrestart
- updatename — update file name
- Command example:
wusa.exe "%cd%\kb4012212-x64.msu" /quiet /warnrestart
- The command initiates a silent installation of the update. Upon installation, it shows the notification on computer restart and gives about a minute to save the open files (there is no option to proceed without restart).
- As a result, you must have a temporary folder with the bat file and the required msu files.
Please note: there will be no negative consequences if you run the command on a computer where the update is already installed or is incompatible
- In Kaspersky Security Center, go to Advanced → Remote installation → Installation packages. In the right frame, click Create installation package.
- In the New Package Wizard, select Create installation package for specified executable file.
- Create the installation package with the .bat file. Select the check box Copy entire folder to the installation package to include the .msu files to the package.
Additional: In the bat file, you can also specify installation of several updates and put these updates’ files into the temporary folder, but this will increase the size of the package.
- Install the created package to the computers. You can choose the computers to which the update will be installed by their operating system type (select the group of computers and select Install application in the right-click menu). Or, you can create a task for a group of computers (select a group or the whole node in the Managed computers section, on the Tasks tab, create the installation task). You can also install the package in any other way you are used to.
Local installation of the package is also available.
Alternative way:
Required:
- Extended license for the Kaspersky product.
- Use of the Search for Microsoft updates and vulnerabilities task.
Process:
- Go to Additional → Manage applications → Update.
- In the search line, find the required Microsoft update.
- Right-click the update and select Install Update.
- Install the update on all the computers that require this action.
How to use the computers safely without installing the Microsoft update
For secure use of the computers without installing the Microsoft update, do the following:
- Disconnect the computer from the corporate network (unplug the Ethernet cable).
- In the server properties, go to the General tab and select Disabled for the Status type.
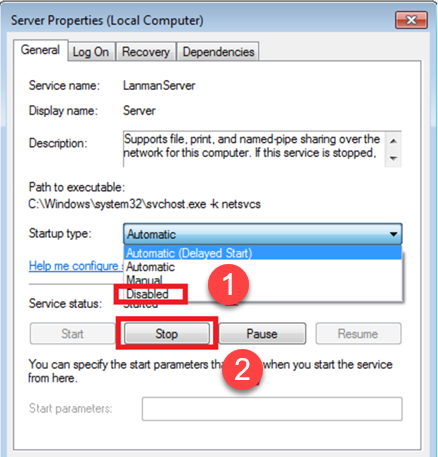
- Plug in the Ethernet cable and run an operating system update with all required restarts.
Make sure that the system does not offer to install any updates.
- After that, you can enable the Server service.
- Make sure the following components are enabled in Kaspersky Endpoint Security:
- File Anti-Virus
- System Watcher
- Network Attack Protection
Useful references
Free ransomware decryptors
WannaCry: What you need to know
WannaCry: Are you safe?