How to install Kaspersky Security for Virtualization 6.x Agentless in an infrastructure managed by VMware NSX-T Manager
Before installing the application, make sure that:
- SVM (Secure Virtual Machine) images are received from a trusted source. For instructions, see this article.
- Agent VM Settings are configured for each hypervisor: network and storage for service virtual machines and the SVM. To learn more about configuring Agent VM Settings, see VMware documentation.
- If the N-VD type of switch is used, one physical network interface is reserved for N-VDS configuration on each hypervisor.
To install Kaspersky Security for Virtualization 6.x Agentless in an infrastructure managed by VMware NSX-T Manager, complete the steps below in the VMware NSX Manager web console.
1. Register the NSX Manager
Register VMware vCenter Server as the NSX Manager:
- Go to System → Fabric → Compute Managers.
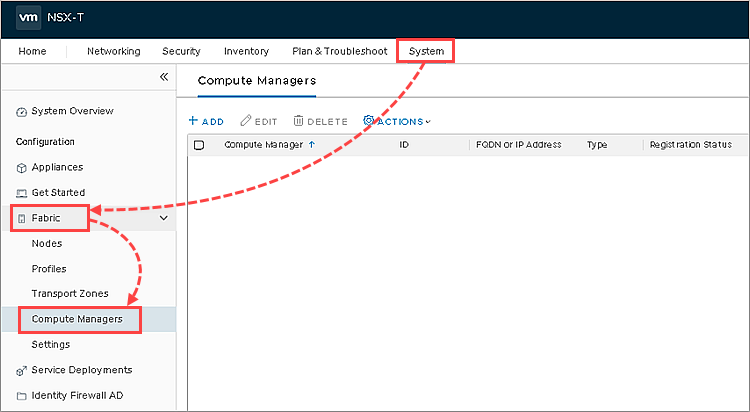
- Click Add.
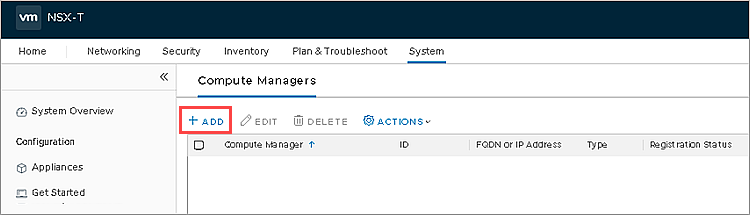
- Specify the account for connecting VMware NSX-T Manager to VMware vCenter Server and connection parameters. Click Add.
Once registration is complete, the following statuses will be displayed in the table for VMware vCenter Server:
- Registration Status — Registered.
- Connection Status — Up.
2. Create a profile for the NSX transport node
- Go to System → Fabric → Profiles.
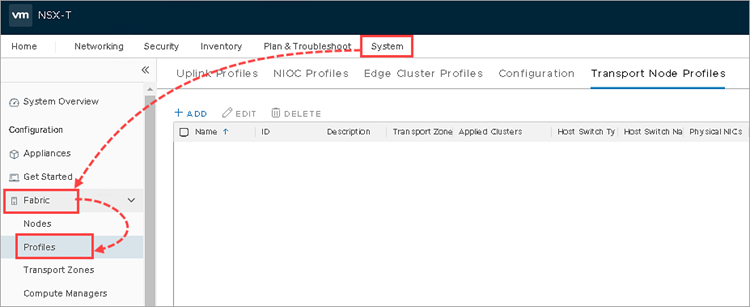
- Go to the Transport Node Profiles tab and click Add.
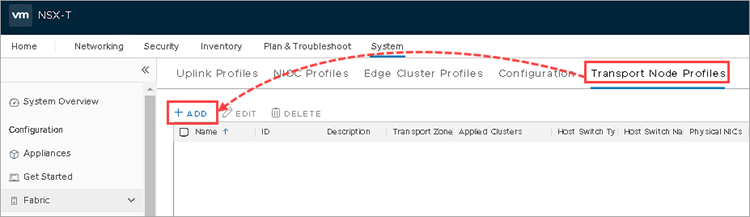
- Specify the parameters:
- Name — set the name for the new NSX transport node profile.
- Type — switch type. If you want to use the VDS type switch, create Distributed Virtual Switch within your Datacenter first.
- Mode — Standаrd.
- Name — enter the name depending on the switch that you will be using. If you have selected N-VDS — enter a new name for the switch that will be created when the NSX transport profile is applied on VMware ESXi hypervisors. If you have selected VDS — the name of the VMware vCenter Server and the Distributed Virtual Switch.
- Transport Zone — NSX transport zone of the Overlay type, to which SVMs are connected.
- Uplink Profile — nsx-default-uplink-hostswitch-profile.
- IP Assignment (TEP) — method of assigning IPIP addresses in your virtual infrastructure: by DHCP protocol or from the static pool of IP addresses. If you are using static pools of IP addresses, first configure and select the pool of IP addresses for the tunnel endpoints on hypervisors.
- Teaming Policy Uplink Mapping — if you have selected the N-VDS switch type, specify the physical network interface based on which the N-VDS switch will be created.
- Click Add.
The NSX transport profile will be created.
3. Prepare VMware ESXi hypervisors for protection deployment.
Install VMware NSX components:
- Go to System → Fabric → Nodes.
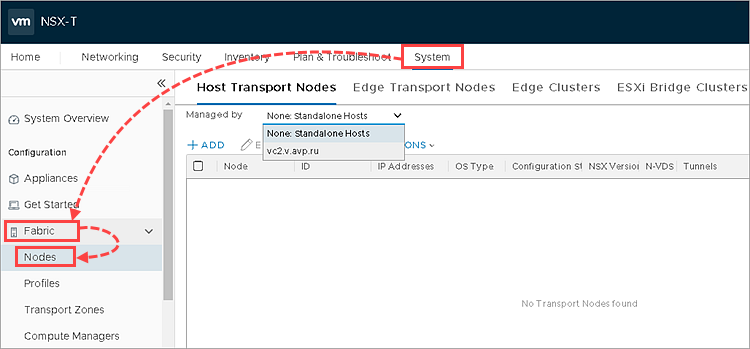
- Go to the Host Transport Nodes tab.
- In the Managed By drop down list select the VMware vCenter Server you have added.
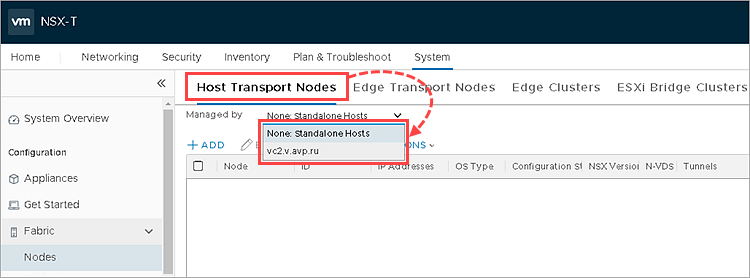
- Select the cluster with the hypervisors on which you want to deploy an SVM.
- Click Configure NSX.
- Select the NSX transport profile created at step 2.
- Click Apply and wait until the hypervisors are prepared.
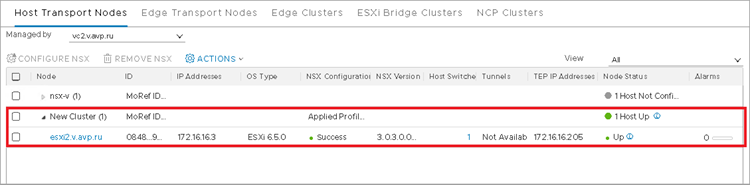
Hypervisors will be ready for protection depoyment.
4. Check the NSX Data Center license
To use the Network Threat Protection component, you will need on of the following licenses:
- NSX Data Center Advanced
- NSX Data Center Enterprise Plus
- NSX Data Center for Remote Office Branch Office
- NSX for vSphere Advanced
- NSX for vSphere Enterprise
By default, a standard NSX for vSphere license is added upon deployment of VMware NSX-T Manager. If you use a standard license, the Network Service Insertion (Third Party Integration) feature, which is required for enabling Network Threat Protection on VMware ESXi hypervisors, is unavailable.
To view the information about the licenses in use, go to System → Licenses.
If there is no license from the list above, add it using the license wizard.
5. Create the NSX segment for Network Threat Protection
- Go to Networking → Segments.
- Click Add Segment.
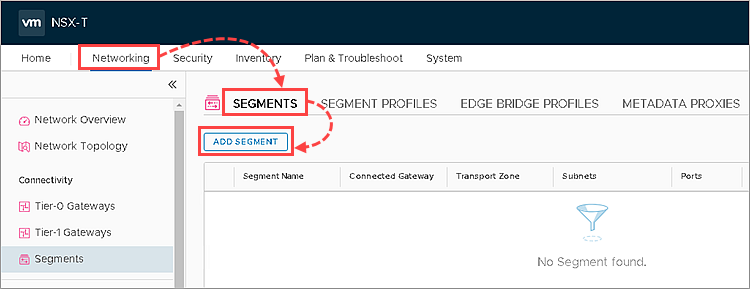
- In the Segment Name column enter the name for the new NSX segment.
- In the Transport Zone column, select the NSX transport zone in which you have created the NSX transport profile at step 2.
- Click Save.
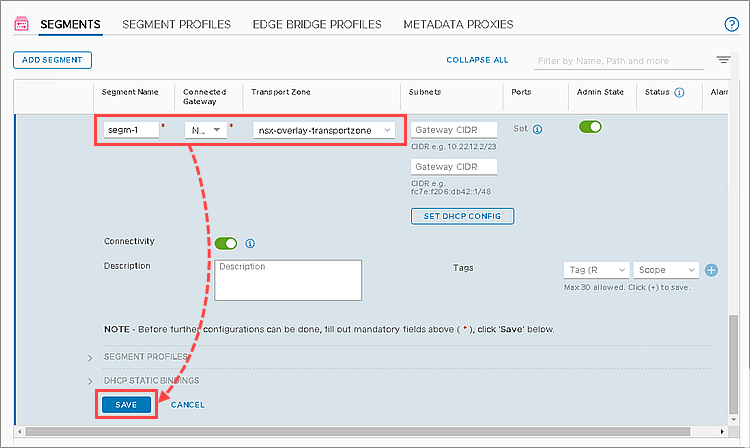
The NSX segment will be created. Connect the network interfaces of virtual machines that you want to protect against network threats. To do this, go to the virtual machine properties in the VMware vSphere Client console.
6. Register Kaspersky Security services in VMware NSX-T Manager
- Publish all the SVM images with Kaspersky Security for Virtualization 6.x Agentless components on a file server with network access via HTTP or HTTPS. You can use the IIS web server integrated in Windows.
- Install Kaspersky Security Center components: management plugin, the Integration Server console and the Integration Server. See the Online Help page for instructions.
- Specify the settings of the Integration Server connection to VMware vCenter Server. See the Online Help page for instructions.
- Enter the settings required for registration and deployment of Kaspersky Security services in the Wizard that is started from the Integration Server Console. See the Online Help page for instructions.
Kaspersky Security services will be registered in VMware NSX-T Manager.
7. Review the list of registered services
The integration server will be registered in VMware NSX Manager as Kaspersky Service Manager
To view the list of registered services:
- Go to System → Service Deployments.
- Go to the Catalog tab.
- Check the services Kaspersky File Antimalware Protection and Kaspersky Network Protection are in the list. If they aren’t in the list, repeat step 6.
8. Deploy SVMs with the File Threat Protection component
To deploy the SVMs with the File Threat Protection component on VMware ESXi hypervisors, deploy the Kaspersky File Antimalware Protection service on VMware clusters:
- Go to System → Service Deployments.
- Go to the Deployment tab.
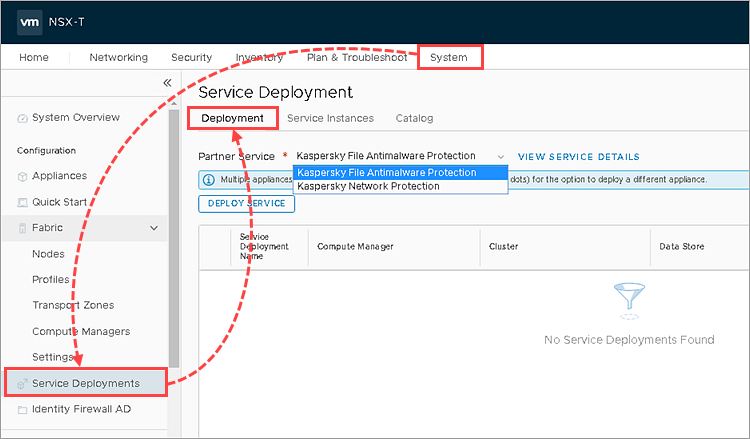
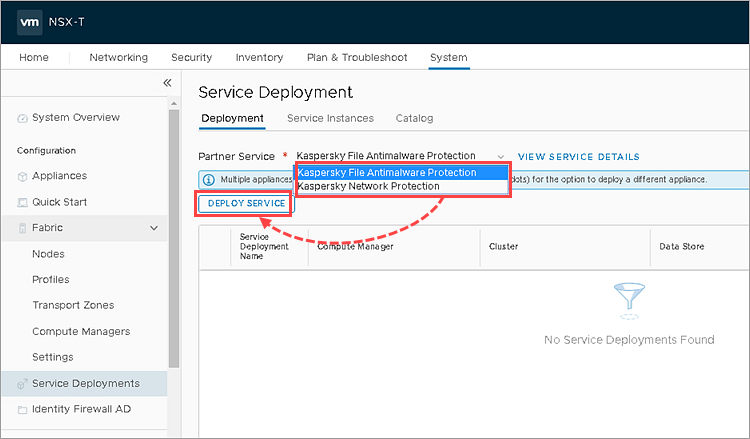
- In the Partner Service field, select Kaspersky File Antimalware Protection.
- Click DeployService.
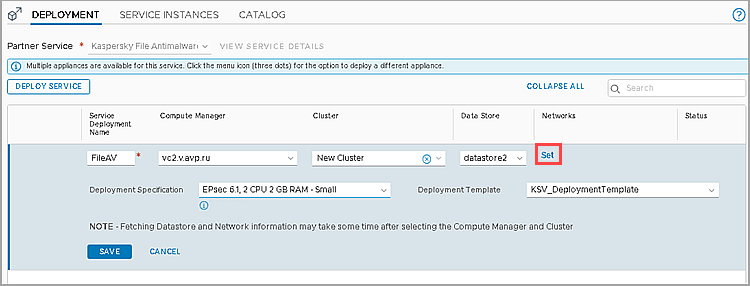
- Specify the parameters for deployment:
- Service Deployment Name — set a deployment name.
- Compute Manager — VMware vCenter Server, to which the VMware NSX-T Manager is connected.
- Cluster — Vmware cluster on which you would like to deploy the SVMs with the Network Threat Protection component.
- Data Store — storage for SVM deployment.
- Deployment Specification — configuration of the SVMs with the File Threat Protection component that will be deployed on hypervisors (Small, Medium or Large, for more information about configurations, see Online Help).
- Deployment template — KSV_DeploymentTemplate.
- Click Set in the Networks column.
- Adjust the network parameters:
- In the Network column of the network interface eth0 specify the network that will be used by the SVM, and in the Network Type field indicate the way to assign IP addresses.
- To use a static IP address, specify the pool of IP addresses in the IP Pool column.
To create a pool, click ManageIPPools and configure the pool from which the SVM IP addresses will be assigned. - Select the checkbox to the left from the eth1 interface name.
- Click Save.
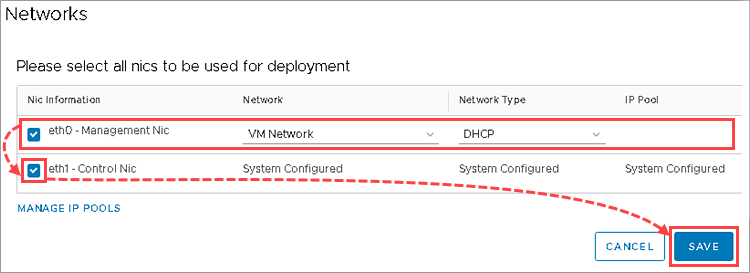
- Click Save to start SVM deployment.
- Wait until Kaspersky File Antimalware Protection is successfully deployed. If the Kaspersky File Antimalware Protection service is successfully deployed, the Status column will show the value Up.
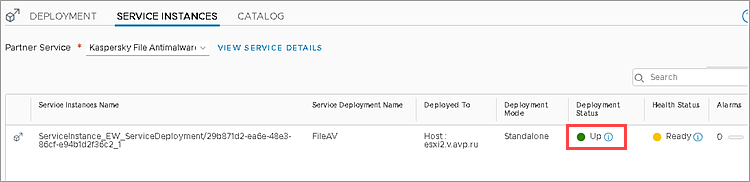
- Go to the Service Instances tab.
- Make sure the SVMs have been deployed successfully on each hypervisor in the VMWare cluster you selected.
The SVMs with the File Threat Protection component will be deployed.
You can also check the deployed SVMs in the VMware vSphere Client console.
9. Deploy SVMs with the Network Threat Protection component
To deploy SVMs with the Network Threat Protection component on VMware ESXi hypervisors:
- Go to System → Service Deployments.
- Go to the Deployment tab.
- In the Partner Service drop-down list, select the Kaspersky Network Protection service.
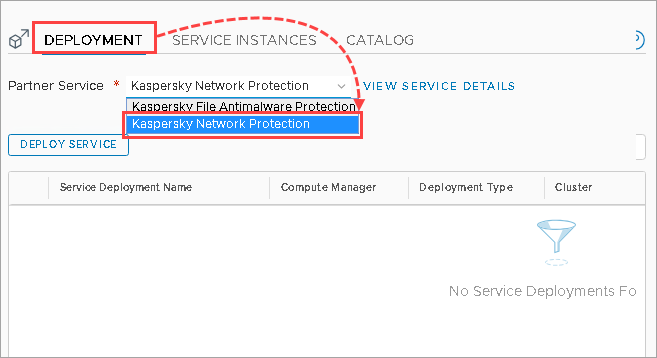
- Click DeployService.
- Specify the parameters for deployment:
- Service Deployment Name — set a deployment name.
- Compute Manager — VMware vCenter Server, to which the VMware NSX-T Manager is connected.
- Deployment Type — method of deployment for SVMs with the Network Threat Protection component.
If you select Host Based, SVMs will be deployed on each hypervisor in the selected VMware cluster. When a new hypervisor is added to the cluster, an SVM will be deployed on it as well.
If you select Clustered, the number of SVMs that you will specify in the Clustered Deployment Count will be created in the specified Vmware cluster. In the Host field you can specify the hypervisor on which these SVMs will be deployed. If Any is selected in the Host field, the hypervisors on which the SVMs will be deployed will be assigned automatically. - Cluster — VMware cluster on which you would like to deploy the SVMs with the Network Threat Protection component.
- Data Store — storage for SVM deployment.
- Deployment Specification — configuration of the SVMs with the Network Threat Protection component that will be deployed on hypervisors (for more information about configurations, see Online Help).
- Deployment template — KSVNS_DeploymentTemplate.
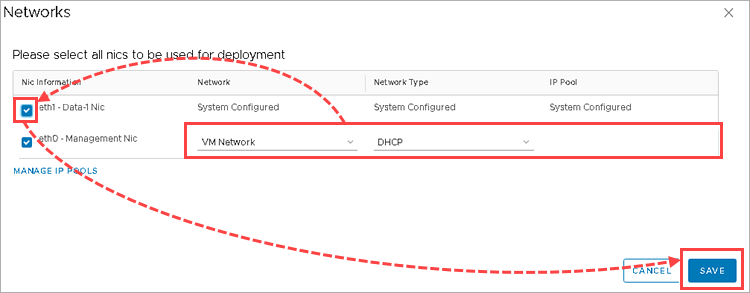
- Click Set in the Networks field.
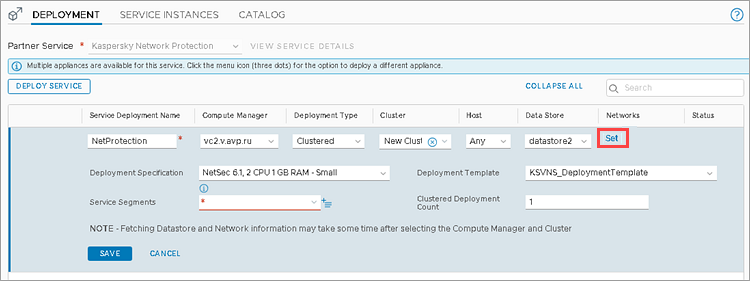
- Adjust the network parameters:
- In the Network column of the eth0 network interface specify the network that will be used by the SVM.
- In the Network Type column of the eth0 network interface specify the method of assigning IP addresses.
- To use a static IP address, specify the pool of IP addresses in the IP Pool column. To create a pool, click ManageIPPools and configure the pool from which the SVM IP addresses will be assigned.
- Select the checkbox to the left from the eth1 interface name.
- Click Save.
- Click
 сto the right of the Service Segments drop-down list.
сto the right of the Service Segments drop-down list.
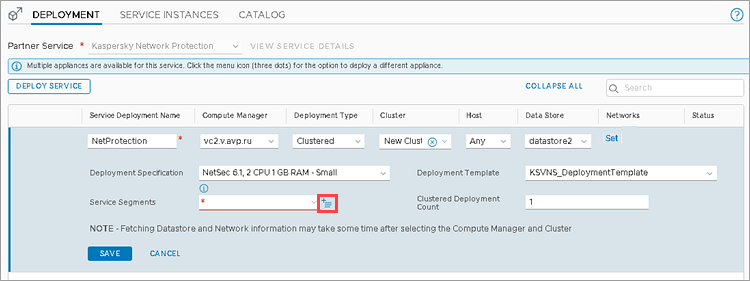
- Click Add Segment. Set the name for the NSX service segment, specify the NSX transport zone and click Save.
- Click Close.
- Select the created NSX service segment in the Service Segments field.
- Click Save to start SVM deployment.
- Wait until Kaspersky Network Protection is successfully deployed. If the Kaspersky Network Protection service is successfully deployed, the Status column will show the value Up.
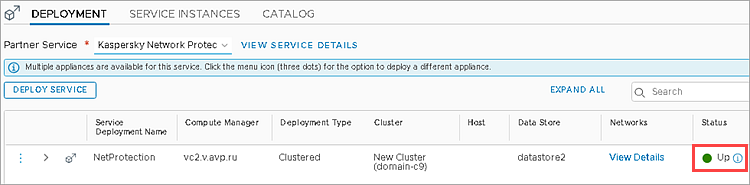
- Go to the Service Instances tab.
- Make sure the SVMs have been deployed successfully on each hypervisor in the VMWare cluster you selected.
The SVMs with the Network Threat Protection component will be deployed.
You can also check the deployed SVMs in the VMware vSphere Client console.
10. Configure NSX groups
Add the virtual machines you want to protect with Kaspersky Security for Virtualization 6.x Agentless to one or several NSX Groups. First, create the NSX groups and adjust the rules for adding VMs to the group, using:
- Adding SVMs to the NSX Security Group dynamically. The group will include all the virtual machines that meet the specified criteria.
- Adding specified VMs.
You can combine these options when configuring the rules of adding SVMs to the NSX Group. For example, you can select adding the VMs to the group according to specified parameters dynamically and also specify the VMware management objects to be included into the group.
To configure the NSX group:
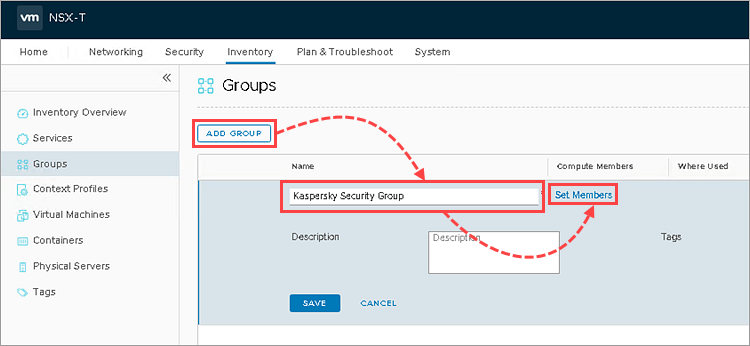
- Go to Inventory → Groups.
- Click Add Group.
- Enter a name for the new NSX Group. For example: Kaspersky Security Group or Protected by Kaspersky.
- Click Set Members.
- If you want to set dynamic adding of virtual machines into the group:
- Go to the Membership Criteria tab.
- Click Add Criteria.
Adjust the criteria for adding the VMs to the group. For example, if you want to add to the group all the virtual machines running Windows, set the Virtual Machine, OS, Name, Contains, Windows criteria.
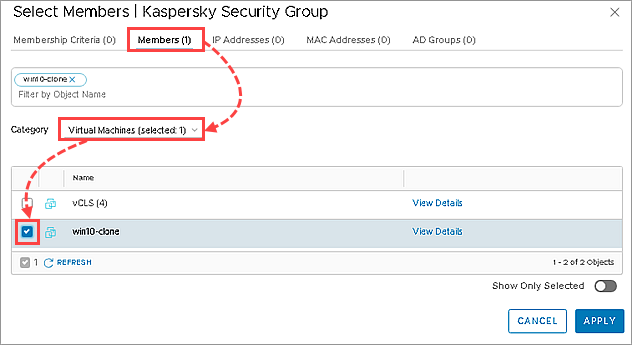
- If you want to specify the virtual machines to add to the NSX Group:
- Go to the Members tab.
- In the Category drop-down list, select Virtual Machines.
Select the virtual machines that you want to add into the group.

- Click Apply →Save.
- Click View Members and make sure that the virtual machines you want to protect are included in the NSX Group.
The NSX Groups will be configured.
11. Configure NSX policies for File Threat Protection
To use File Threat Protection on virtual machines included into the NSX group, create the NSX profile for the Kaspersky File Antimalware Protection service and configure the NSX policy for the NSX group:
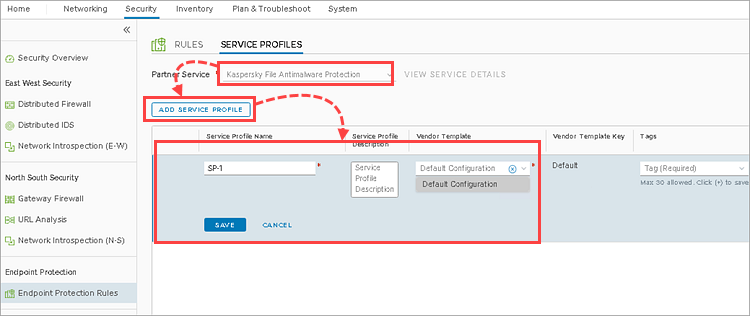
- Go to Security →Endpoint Protection Rules.
- Go to the Service Profiles tab.
- In the Partner Service drop-down list, select the Kaspersky File Antimalware Protection service.
- Click AddServiceProfile specify the following:
- Service Profile Name — set a name for the NSX service profile.
- Vendor Template — Default Configuration template.
- Click Save.
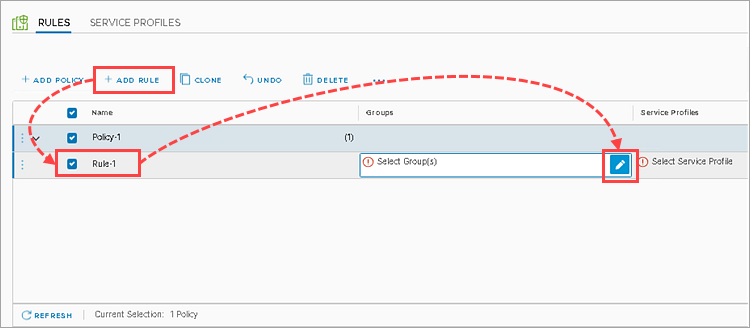
- Go to the Rules tab and click AddPolicy.
- Give a name to the policy in the Name column, select the policy and click AddRule.
- Give a name to the rule in the Name column and click
 in Select Groups.
in Select Groups.
- Choose one or several NSX groups ithat contain SVMs. Click Apply.
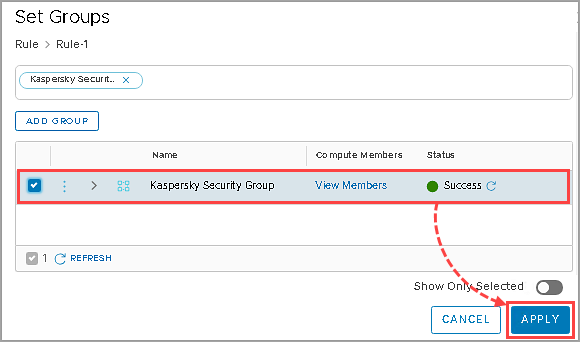
- Click
 in the Select ServiceProfiles field.
in the Select ServiceProfiles field.
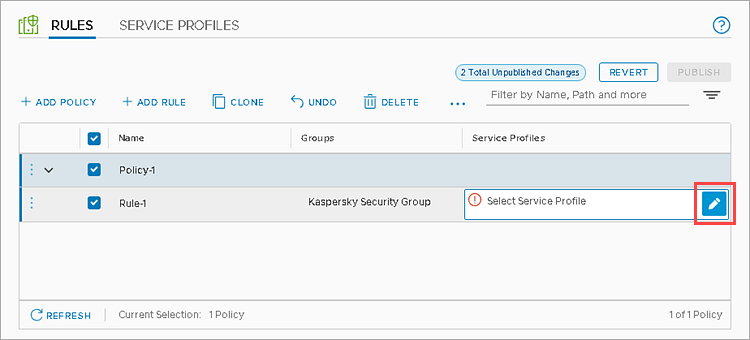
- Select the created Kaspersky File Antimalware Protection service profile and click Save.
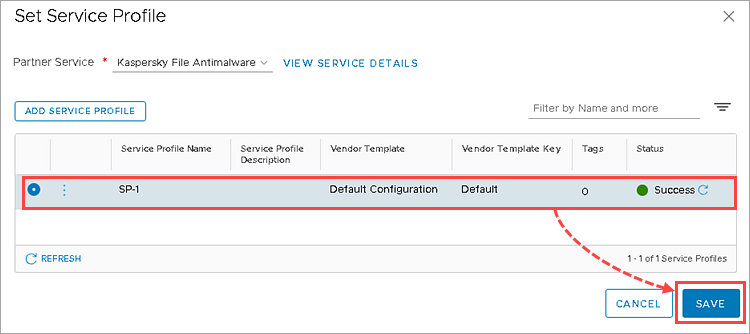
- Click Publish.
The NSX Policy will be applied to the NSX Group.
12. Configure NSX policies for Network Threat Protection
For network threats protection of virtual machines included into the NSX group, follow the following steps:
Step 1. Create the NSX service profile for the Kaspersky Network Protection service
- Go to Security → Network Introspection Settings.
- Go to the Service Profiles tab.
- In the Partner Service drop-down list, select the Kaspersky Network Protection service.
- Click Add Service Profile and specify the following:
- Service Profile Name — set a name for the NSX service profile.
- Vendor Template — Default Configuration template.
- Click Save.
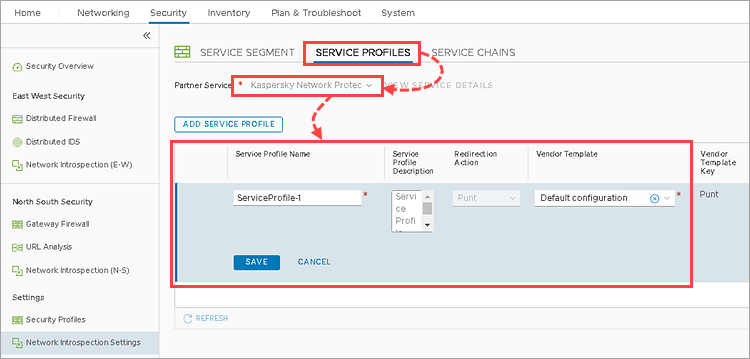
Step 2. Create the NSX service chain
- Go to Security → Network Introspection Settings.
- Go to the Service Chains tab.
- Click Add Chain and specify the following:
- Name — set a name for the NSX service chain.
- Service Segments — the NSX service segment that you have specified for deployment of SVMs with the Network Threat Protection component.
- Reverse Path — make sure the Inverse Forward Path checkbox is selected.
- Failure Policy — Allow.
- Click Set Forward Path.
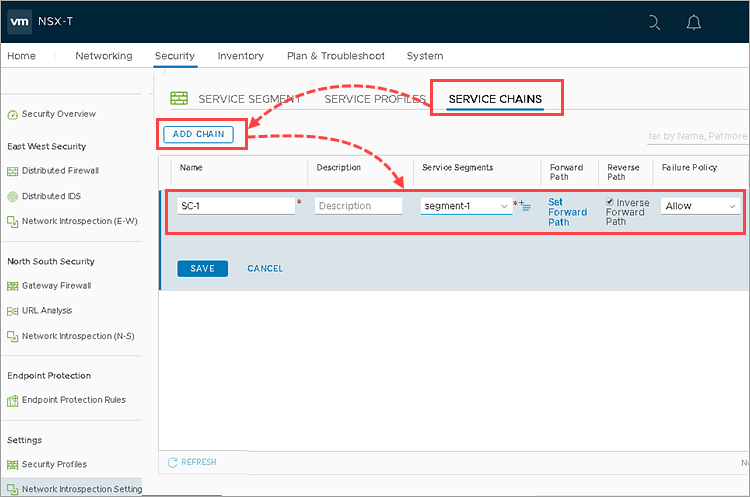
- Click Add profile in sequence and select the created Kaspersky Network Protection service profile.
- Click Add →Save.
- Click Save.
Step 3. Configure the policy for the NSX group
- Go to Security→ Network Introspection (E-W), click Add Policy and specify the following parameters:
- Name — set a policy name.
- Redirect To — select the NSX service chain that you have created.
- Click Publish.
- Check the incoming traffic of the virtual machines:
- Select the created policy and click Add Rule.
- Give a name to the rule in the Name field and click
 in the Destinations field.
in the Destinations field. - Choose one or several NSX groups that contain SVMs and click Apply.
- Click the icon in the Applied To field.
- Select Groups as a type of object to which the rule is applied, select one or several NSX groups that contain SVMs and click Apply.
- Click Publish.
- Check the outbound traffic of the virtual machines:
- Select the created policy and click Add Rule.
- Give a name to the rule in the Name field and click
 in the Destinations field.
in the Destinations field. - Choose one or several NSX groups that contain SVMs and click Apply.
- Click the icon in the Applied To field.
- Select Groups as a type of object to which the rule is applied, select one or several NSX groups that contain SVMs and click Apply.
- Click Publish.
The NSX Policy will be applied to the NSX Group.
